Analyzing the Assembly from Modern Warfare II (2022) campaign
This was originally posted to the Modern Warfare II subreddit, but it was deleted by the moderators for being off-topic :(
Some of you probably noticed that the missile control computers – where you got asked to read the first letter of the second row and first column, etc – had Assembly code shown.
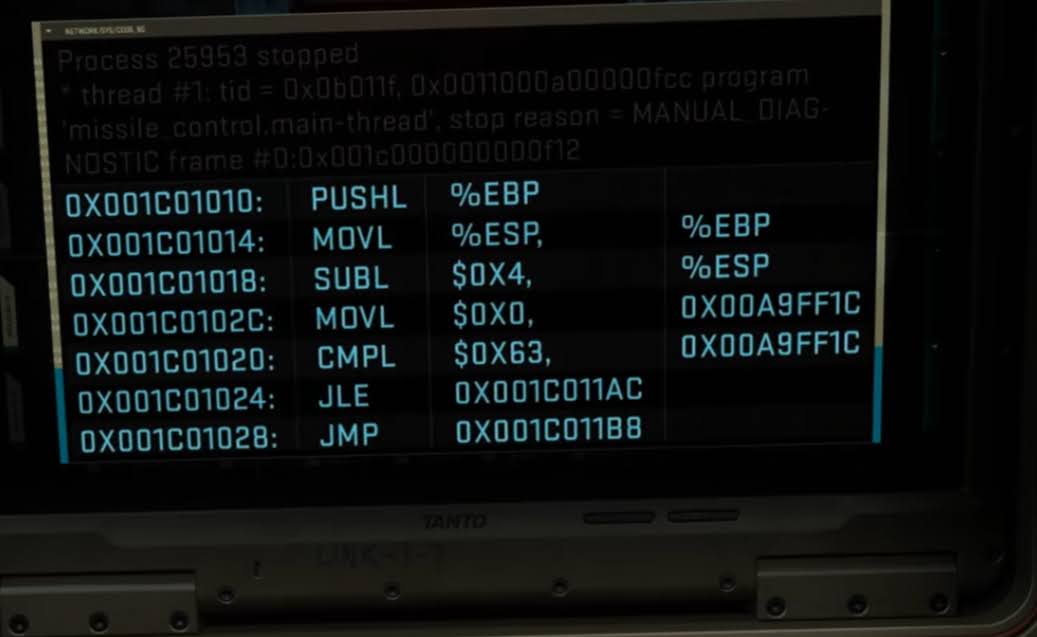
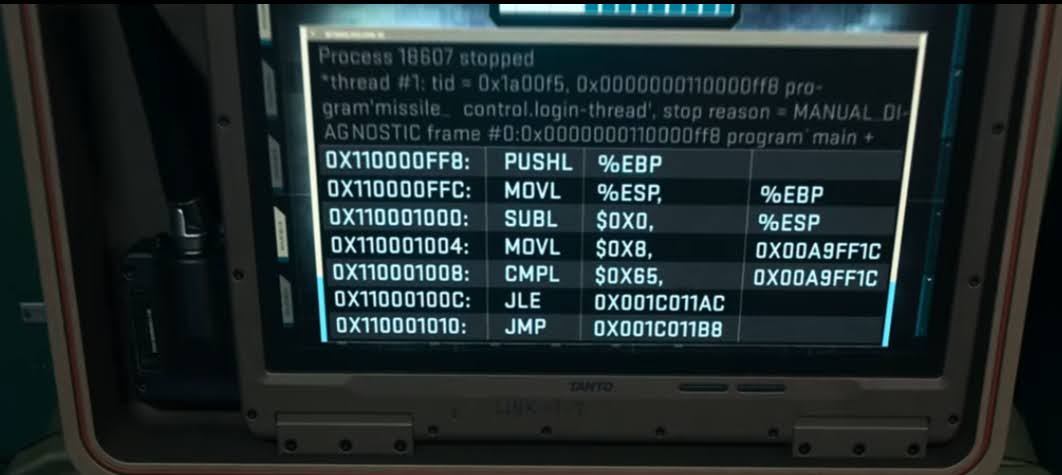
I wanted to actually check if the Assembly made sense and was valid or if it was just garbage (ala /r/ItsAUnixSystem).
Here’s my annotated version* of the Assembly shown in the last mission
;Put the base/frame pointer onto the top of the stack
PUSHL %EBP
;Make the base pointer point to the address of the stack pointer
MOVL %ESP, %EBP
;Lower the stack pointer by exactly 4 bytes. On x86 the stack "grows" down,
;so it has to be decremented to make room for additional variables.
SUBL $0x4, %ESP
;"Zero out" the memory at address 0x00A9'FF1C
MOVL $0X0, 0x00A9FF1C
;Sets up a comparison between:
;* the contents of memory address 0x00A9'FF1C
;* 0x636 (1590 in decimal).
CMPL $0x636, 0x00A9FF1C
; In the previous instruction, we compared the two values
; (the result of that comparison is stored in separate registers)
; This instruction is saying, if 0x636 is less than the value stored at address 0x00A9'FF1C,
; then "jump to" (i.e. set the program counter) address 0x001C'011AC
JLE 0x001C011AC
; Finally, jump to memory address 0x001C011B8
JMP 0x001C011B8This looks like a valid snippet so far.
And the first example, which is from the “Dark Water” mission:
PUSHL %EBP
MOVL %ESP, %EBP
; It's kind of odd that this is here, since it's basically a useless instruction.
; Unless it was done intentionally to show that there's no local variables going to be used.
SUBL $0x0, %ESP
MOVL $0x8, 0x00A9FF1C
CMPL $0x65, 0x00A9FF1C
JLE 0x001C011AC
JMP 0x001C011B8This is very similar to the other snippet – using the same instructions, just some different values. Seems to mostly check out. Good job Infinity Ward.
Leave a comment